The Virtual Private Networking (VPN) service allows you to connect to the NJIT network from off-campus using the Internet Service Provider (ISP) of your choice. VPN allows you to securely access NJIT network resources from anywhere at any time. NJIT supports Cisco's AnyConnect VPN, which is compatible with a wide variety of devices. Jon Langemak December 13, 2009 December 13, 2009 1 Comment on Cisco Anyconnect and WebVPN AnyConnect and WebVPN are perhaps the best features of the ASA appliances in my mind. Before we dive into the Anyconnect and WebVPN “How to” I thought it might be best to give a brief description of what each feature is and how they work together.
We have resisted the change for a long time, bit its time to finally move some of our customers over to the SSL VPN who were previously using the IPSec Remote Access VPN. Windows 10 does not support the IPSec client any more, Cisco have stopped developing it and its only saving grace is that Mac seem to have no problem with the built in VPN connector.
We are moving some clients to the ASAv which I will document the installation of another time, but the software version I am using is 9.6(1).

Requirements:
1. Most users will be standard, tunnel-all users
2. A few users will require local LAN access for IP printers etc. These will be kept to a minimum as they pose a security risk
3. The Anyconnect software should be deployed from the ASA.
4. The users will all be stored in the ASA local database.
Software Download - Cisco Systems
Stage 1 – Get a 3rd party certificate
I have a previous post on this which is still valid. I used a RapidSSL from Geotrust. The latest client has a ‘checked’ check box to disable non trusted certificates by default and could cause a lot of pain for the support guys – so do this first! make sure the time is set as per the article.
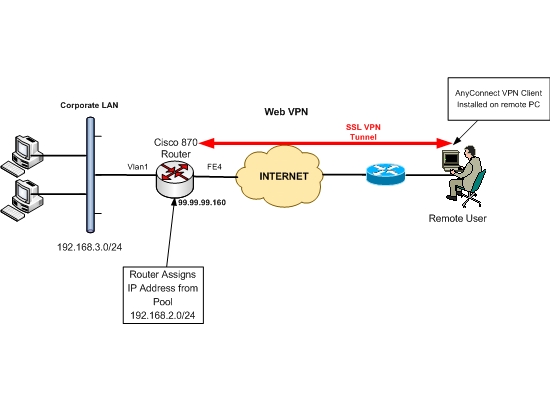
Stage 2 – Create an IP pool for the remote users
I favour using a completely separate IP range, not used anywhere else on the internal network. This saves a lot of faff with adding routes later.
ip local pool VPN-POOL 10.11.11.1-10.11.11.50
Stage 3 – Sort the NAT out

I ran into a world of pain when i did this first as the ASA started responding to ARP requests from anything on its OUTSIDE subnet. The take-home message is that avoid using ‘any’ in your NAT setup. So we want to define the POOL as an object and use that to get the NAT exemption for data leaving our ‘INSIDE’ network to the ‘OUTSIDE’ network via the VPN tunnel. Also we want traffic coming back from the client, not destined for the INSIDE network to be NATted to the internet.
object network VPN-IP-POOL
subnet 10.11.11.0 255.255.255.0
nat (OUTSIDE,OUTSIDE) dynamic interface dns
Now the NAT exemption for the INSIDE to OUTSIDE traffic. I assume there is already a LAN object defined.
nat (INSIDE,OUTSIDE) source static LAN LAN destination static VPN-IP-POOL VPN-IP-POOL
Also we’ll need to allow the OUTSIDE traffic to hairpin on the interface.
same-security-traffic permit intra-interface
Stage 4 – Add the webvpn config
Here we need to upload the pkg files which can be downloaded from cisco.com into the flash of the ASA. they are then referenced in the config.
webvpn
enable OUTSIDE
anyconnect image disk0:/anyconnect-win-4.2.05015-k9.pkg 1
anyconnect image disk0:/anyconnect-macosx-i386-4.2.05015-k9.pkg 2
anyconnect image disk0:/anyconnect-linux-64-4.2.05015-k9.pkg 3
anyconnect enable
tunnel-group-list enable
Note the pkg references have an index number to permit multiple files to be uploaded.
Stage 5 – Group Policy
Cisco Asa Anyconnect Webvpn
We’ll create a Group Policy to set the parameters for the users. Its best to create a new policy rather than edit the default. This is our ‘tunnel-all’ policy which will be referenced by the tunnel group as the default policy.
group-policy CUSTOMER-POLICY internal
group-policy CUSTOMER-POLICY attributes
dns-server value 8.8.8.8
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelall
Stage 6 – The Tunnel Group
Here a tunnel group is created which pulls it all together
tunnel-group CUSTOMER type remote-access
tunnel-group CUSTOMER general-attributes
address-pool VPN-POOL
default-group-policy CUSTOMER-POLICY
tunnel-group CUSTOMER webvpn-attributes
group-alias CUSTOMER-LOGIN enable
The group aliases appear in the dropdown when the user logs in.
Stage 7 – The Users
AnyConnect VPN Client FAQ
The users are all using the default group policy of ‘CUSTOMER-POLICY’ unless we specify differently.
username user_name password pass_word
username user_name attributes
vpn-group-policy MY-DIFFERENT-GROUP-POLICY
group-lock value CUSTOMER
service-type remote-access
I’ve also locked the user into the correct group to be secure.
This is enough to get up and running – there is loads more to do with customisation, additional security and the like, but for now the customer needs to get online.
